APTs Under the Microscope: Identifying Hostile Tools with Batuta
July, 8, 2025
5 minutes read

Advanced Persistent Threats (APTs) don’t always rely on custom malware. Groups like APT29 (Cozy Bear), APT41, and Lazarus Group have demonstrated that using legitimate tools such as remote administration software (RMM), network utilities, or native scripts can be just as effective in maintaining persistence and evading traditional defenses.
Recently, the use of RMM (Remote Monitoring and Management) tools like AnyDesk, TeamViewer, or even MSP-focused tools like ConnectWise have surged as a vector for abuse. This is largely because they provide legitimate, encrypted access with advanced functionalities that often go undetected by antivirus or EDR solutions.
According to the 2024 Red Canary Intelligence Report, RMM tools have become a common tactic among both sophisticated actors and opportunistic criminals, particularly for remote execution, lateral movement, and covert exfiltration of sensitive data.
Developing Risky Application Detection Policies
Thanks to the knowledge and experience of our Threat Intelligence, Threat Hunting, Red Team, SOC, and Incident Response experts, we have developed a robust set of policies aimed at identifying applications that could pose a significant risk if present in an organization’s operating systems. This risk is especially heightened when such tools have not been previously authorized or approved through internal software control processes.
These applications, although often legitimate, are widely used by malicious actors to compromise corporate environments. Therefore, their presence must be carefully monitored, analyzed, and controlled, particularly in contexts where infrastructure security and integrity are top priorities.
With Batuta, we have designed a specific set of detection policies focused on potentially hostile tools, grouped into six key categories that reflect techniques commonly used in real-world intrusion campaigns:
- Credential Theft: Tools designed to extract credentials from the system, such as Mimikatz or LaZagne, are widely used by attackers for lateral movement or privilege escalation.
- Defense Evasion: Utilities aimed at evading security mechanisms by disabling EDRs, bypassing UAC, or modifying system behavior to avoid detection.
- Discovery: Network scanners like Nmap or Angry IP Scanner, which attackers use to map the network and gather critical information about available services and hosts.
- Exfiltration: Tools and scripts used to compress, encrypt, and transfer data outside the corporate environment, often via PowerShell, covert network protocols, or cloud storage.
- RMM and Network Tools: Remote access solutions, such as AnyDesk, TeamViewer, ConnectWise, or VNC, can be exploited by both administrators and attackers to maintain persistence and remote control over compromised systems.
- Offensive Security: Advanced penetration testing platforms such as Cobalt Strike, Metasploit, or Empire, whose uncontrolled use in production environments indicates compromise or suspicious activity.
These policies are designed with a proactive approach not only to identify active threats but also to reduce the attack surface by flagging the presence of tools whose use must be explicitly justified and documented. With Batuta, we help organizations increase their visibility and control, ensuring operational environments align with cybersecurity and compliance best practices.
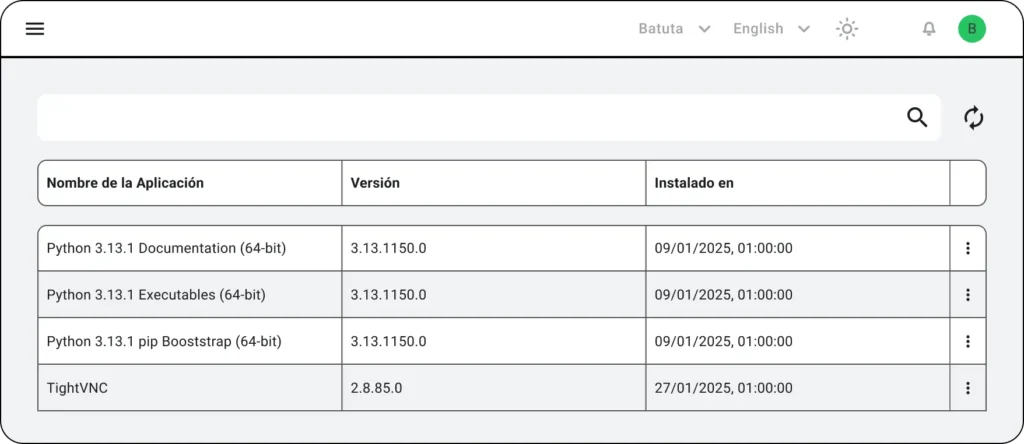
Risky Application Detection
Once software scans are executed via the software inventory module, it’s possible to accurately identify devices that contain applications considered risky or unauthorized by the organization.
Through periodic and continuous reporting, a collaborative validation process is conducted with the heads of each area or operational unit to confirm which applications are justified in their use and which hosts should have them restricted. This stage is crucial to ensure policies align with real business needs without compromising operations.
With this consolidated information, scanning and detection policies are fine-tuned and adjusted within Batuta to strengthen proactive identification of applications that pose a potential security risk, whether due to their functionality, origin, or use outside official channels.
This iterative process enables organizations to maintain continuous control over installed software, reduce the attack surface, and ensure the operating environment adheres to defined security and compliance standards.
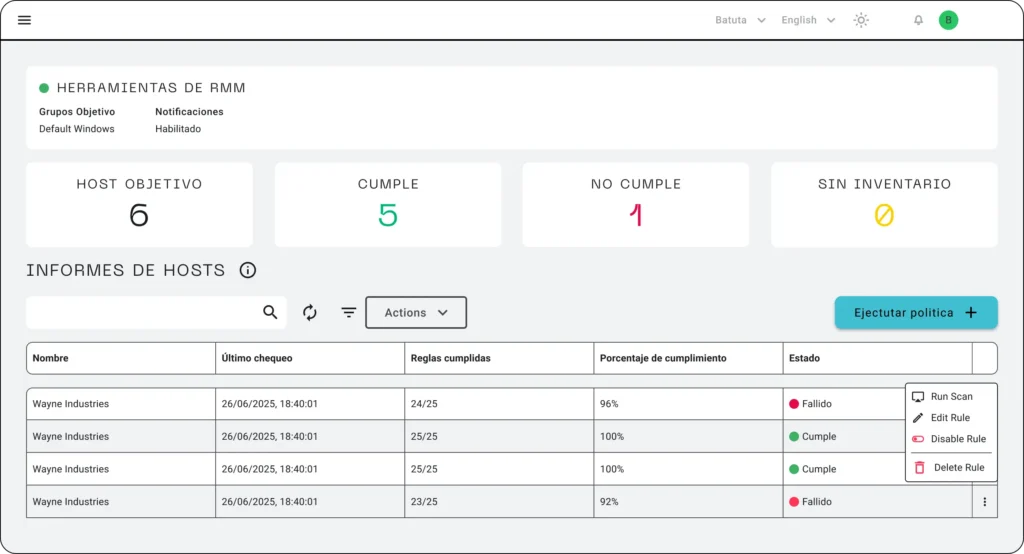
Figure 1. Result of RMM application scanning policy execution
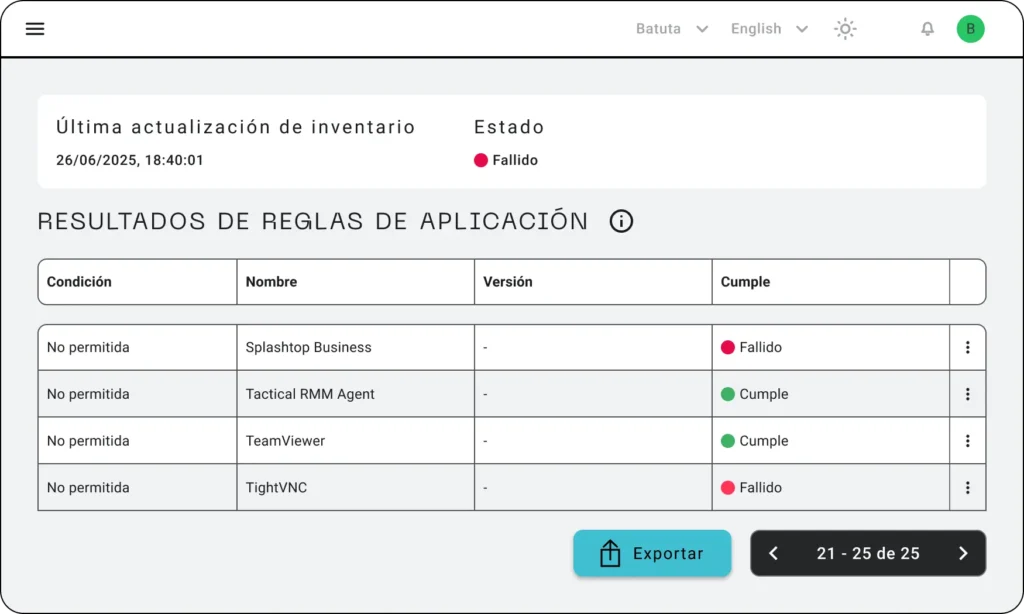
Figure 2. RMM type risky application detection
Response Actions
Batuta identifies potentially risky or unauthorized applications and facilitates the execution of effective response actions to contain and mitigate the risks associated with their presence.
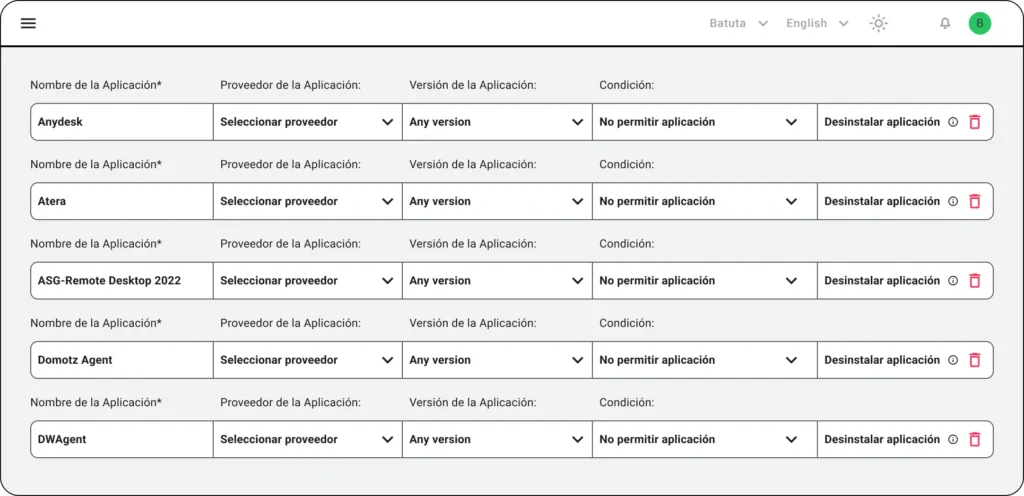
Once applications that need to be removed are validated, Batuta allows their automated uninstallation through two main mechanisms:
- Direct uninstallation from the administration console using the native capabilities of the software inventory module.
- Execution of custom scripts via the script library module, allowing specific actions based on the operating system, type of application, or host context.
Furthermore, Batuta enhances the capabilities of existing Endpoint Detection and Response (EDR) systems by providing contextual intelligence that can be translated into Indicators of Activity (IoAs). These IoAs can be used to:
- Block processes associated with unwanted or malicious applications.
- Restrict network connections initiated by identified risky tools.
- Detect anomalous execution patterns linked to hostile behavior.
Thanks to these capabilities, Batuta becomes an active component in the response cycle, helping organizations not only detect unauthorized software but also act intelligently and automatically to reduce exposure time and improve resilience against internal and external threats.